Running a blog, business, or eCommerce store, your website holds valuable data that cybercriminals are eager to exploit. As cyber threats grow more sophisticated, understanding how to remove malware from website and protect it against future attacks becomes essential. Malware infections not only damage your site’s integrity but also put your visitors, reputation, and search engine rankings at risk.
If website has been flagged by Google, showing unexpected redirects, or if you’re receiving complaints from visitors about strange activity, it may be infected. These attacks are common but manageable—if you act quickly and follow a structured removal and prevention process. Let’s dive into a comprehensive guide to help you clean your website and keep it secure long-term.
Understanding Website Malware: What It Is and Why It Happens
Website malware is malicious code or software injected into your website with harmful intent. It can take many forms—ransomware, trojans, phishing scripts, credit card skimmers, SEO spam, and crypto miners—and each type is designed to either steal sensitive information, hijack your site, or damage its functionality. Hackers typically exploit vulnerabilities in outdated software, plugins, themes, or weak security configurations.
How to Fix Website Downtime Issues Fast – Step-by-Step Guide
Even high-traffic, well-established websites can fall victim to malware. Some malware works quietly in the background for weeks, stealing data or redirecting traffic without your knowledge. In some cases, attackers add backdoors so they can regain access even after being removed. These threats make it clear why understanding how to remove malware from website platforms is so critical, and why prevention is just as important as cleanup.
Signs Your Website Has Been Infected with Malware
Catching the early signs of a malware infection can help you minimize the damage and remove the threat faster. One of the most telling signs is unexpected redirects—visitors may be taken to unrelated or spammy websites without clicking anything. You might also notice unusual pop-ups, especially those promoting fake software or asking for login credentials.
In addition, search engines like Google may flag your site with warnings such as “This site may harm your computer,” severely impacting your traffic and SEO rankings. Suspicious files or scripts—especially ones you didn’t upload—can be found on your server. You may also receive alerts from your hosting provider or monitoring tools indicating suspicious activity. Reduced site performance, database errors, or even locked-out admin access can also suggest a malware breach. Ignoring these signs can allow the infection to spread or become harder to remove.
Step-by-Step Guide: How to Remove Malware from Website
When it comes to removing malware, a systematic approach ensures that nothing is missed and that your site is completely clean. Below is a step-by-step breakdown of the best practices for eliminating threats from your site.
1. Take Your Website Offline Temporarily
The first step in how to remove malware from website setups is to immediately isolate your site. Taking it offline helps prevent your users from being exposed to the malware and stops the infection from spreading further. You can either place your site in maintenance mode using a plugin (for WordPress) or temporarily disable it from your hosting dashboard.
Be sure to notify your users, especially if you run a business, and explain that the site is under maintenance for security reasons. Inform your hosting provider as well—they may offer additional malware scanning or even assist with removal. Also, make a full backup of your site (including files and database), even if it’s infected. These backups can be essential for comparison or restoration later.
2. Scan Your Website for Malware
Next, perform a deep scan to detect the location and nature of the malware. Start with automated tools like Sucuri SiteCheck, Wordfence, MalCare, or VirusTotal. These scanners can quickly identify known malware signatures, backdoors, and malicious scripts injected into your files or database.
For a more thorough analysis, combine automated scanning with manual inspection. Connect via FTP or your file manager and look for recently modified files, base64-encoded strings, hidden iframe tags, and unauthorized admin users in the CMS. Pay special attention to core files and plugins—the infection is often found in index.php, .htaccess, or wp-config.php. If you have a recent clean backup, compare the files side-by-side to locate unauthorized changes.
3. Remove Malicious Code and Infected Files
Once identified, the infected code must be completely removed. Start by deleting suspicious or unknown files from your site’s root directory and subfolders. Open infected files and manually remove malicious code snippets. These may appear as obfuscated JavaScript, strange PHP functions, or base64-encoded text.
If you’re unsure what to remove, it’s often safer to restore clean versions of the core CMS files (like WordPress core) from the official repository. For themes and plugins, delete and reinstall from official sources. It’s highly recommended to work on a staging site if possible so that you can test your changes before going live again. You can also use professional malware removal services like Sucuri or SiteLock if the infection is extensive or difficult to trace.
4. Clean and Restore Databases
Some malware injections target your website’s database, inserting malicious scripts or links into content areas, user tables, or settings. Use phpMyAdmin or your preferred database management tool to visit tables for suspicious content—especially in WordPress tables like wp_options, wp_posts, and wp_users.
Look for base64 code, unfamiliar URLs, or spammy links embedded in post content or settings. You may also find fake admin users or injected redirect scripts. Remove the malicious content carefully, or restore a clean version of the database from a safe backup. Be extremely cautious here—mistakes in the database can break your entire website.
5. Change All Passwords and User Access
Once the malware is removed, you need to secure all access points to your website. Change passwords for:
- Website admin accounts
- FTP/SFTP access
- Hosting control panel
- Database users
- Email accounts associated with your site
Also, audit your CMS user roles. Remove unknown or suspicious users, especially those with admin privileges. Implement strong password policies, and encourage the use of two-factor authentication for extra protection. Leaving old or weak credentials in place creates a serious risk of reinfection.
6. Update Everything: CMS, Plugins, Themes
Outdated software is one of the top entry points for malware. Once your site is clean, immediately update your content management system (CMS), all plugins/extensions, and your theme to their latest versions. This will patch known vulnerabilities that may have been exploited during the attack.
Make sure to delete any unused themes or plugins entirely—deactivating isn’t enough. These files can still be accessed by attackers and serve as a backdoor. Always download plugins and themes from reputable sources, and never use nulled or pirated versions, as they often contain malware.
7. Request Removal from Blacklists
If your site has been blacklisted by Google or flagged as dangerous by browsers, you’ll need to request a security review. Use Google Search Console to find malware warnings under the “Security Issues” tab, then request a review after confirming the site is clean.
Similarly, Bing Webmaster Tools offers malware detection and blacklist removal features. If your antivirus software or hosting provider flagged your site, contact them directly with proof of cleanup. This step is essential to restoring user trust and search engine visibility.
How to Prevent Malware from Coming Back
Removing malware is only half the battle. To prevent future infections, you need to build a robust website security framework. Here’s how to ensure your website stays safe.
1. Install a Website Firewall (WAF)
A Web Application Firewall (WAF) acts as a barrier between your website and malicious traffic. It filters incoming data, blocks IPs known for suspicious activity, and protects against brute force, DDoS, and SQL injection attacks.
Cloud-based WAFs like Cloudflare, Sucuri Firewall, or Astra Security are easy to implement and provide real-time threat protection. Some hosting providers also offer built-in WAFs or server-level firewalls that should be activated. A firewall is one of the best proactive measures against recurring malware infections.
2. Use a Security Plugin for Real-Time Monitoring
Security plugins give you eyes and ears on your website 24/7. Tools like Wordfence, iThemes Security, and Sucuri Security offer malware scanning, login protection, audit logs, file integrity checks, and more. Set them to run automated scans and alert you to changes in critical files.
Enable two-factor authentication (2FA) for all admin accounts and enforce strong password rules. Also, monitor failed login attempts and suspicious behavior to catch potential threats before they escalate.
3. Regular Backups Are a Must
Having recent backups is your best insurance policy. Automate your backup process using tools like UpdraftPlus, BlogVault, or BackupBuddy. These allow you to schedule backups to offsite locations such as Google Drive, Dropbox, or Amazon S3.
Keep multiple backup copies and test them regularly to ensure they can be restored properly. In case your site is compromised again, you’ll be able to recover it quickly without having to repeat the entire malware removal process.
4. Limit File Permissions and Server Access
Misconfigured file permissions can allow hackers to upload malicious files. Ensure that:
- Files are set to 644
- Folders are set to 755
- Configuration files like
.htaccessandwp-config.phpare not writable
Disable directory listing via .htaccess to prevent attackers from browsing your site’s file structure. Restrict access to critical files and disable editing in your CMS dashboard when not needed.
5. Monitor and Audit Website Activity
Regularly audit your website’s user activity and server logs to detect unusual behavior early. Use plugins or server logs to track who logs in, what files are modified, and whether there are unauthorized changes.
You can set up email alerts for suspicious events such as failed login attempts, file changes, or the creation of new admin accounts. These alerts allow you to react quickly if anything unusual happens on your website.
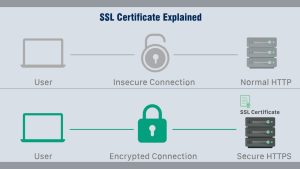
6. Secure Hosting and SSL Certificate
Your hosting environment plays a significant role in your site’s security. Choose a reputable web host with strong security protocols, automated updates, malware scanning, and daily backups. Avoid cheap or shared hosting plans that offer little to no protection.
Also, install an SSL certificate to encrypt communication between your site and visitors. This not only protects data but also boosts SEO and customer trust. Many hosts now offer free SSLs via Let’s Encrypt, so there’s no excuse for not having one.
How to Make Your Website Fully Responsive (Step-by-Step Guide)
A single breach can cost you your SEO rankings, user trust, and even your business revenue. But by following these detailed steps and best practices, you can ensure your website stays clean, professional, and safe for your visitors. In an age where cyber threats are evolving every day, ongoing website security is no longer optional—it’s a necessity.
FAQs
1. What are the common signs that my website has malware?
Common signs include slow website performance, unexpected redirects, unfamiliar pop-ups, blacklisting by search engines, warnings from browsers, unauthorized admin access, or changes to website content without your knowledge. Malware may also trigger spikes in server usage or send spam from your domain.
2. How does malware get onto a website in the first place?
Malware can enter your site through outdated plugins or themes, weak passwords, unsecured file uploads, unpatched CMS vulnerabilities, compromised third-party integrations, or infected user devices. Poor web hosting security can also be a contributing factor.
3. What should be my first step if I suspect malware on my website?
Immediately take your website offline or set it to maintenance mode to prevent further damage or spread. Then, scan your site using a trusted malware scanner, back up current files for analysis, and contact your hosting provider for emergency support.
4. Which tools can I use to scan and remove malware from my website?
Popular tools include Sucuri SiteCheck, Wordfence (for WordPress), MalCare, SiteLock, Google Search Console (Security Issues), and VirusTotal. Many hosting providers also offer integrated scanning and cleanup services.
5. Can I manually remove malware from my website files?
Yes, but it requires technical knowledge. You’ll need to access your website files via FTP or cPanel, identify suspicious code (e.g., base64 encoded scripts), compare with clean backups, and delete or replace the infected files. Always back up everything before making changes.
6. How do I protect my website after removing malware?
After cleanup, update all plugins, themes, and your CMS core. Change all passwords (FTP, database, CMS admin), set up a firewall, install security plugins, limit login attempts, and regularly back up your site. Consider using SSL if not already in place.
7. Will malware affect my search engine ranking or reputation?
Yes. Google may blacklist your site, warn users in search results, or drop your SEO rankings significantly. Malware can also damage your brand’s trust and result in customer data theft, leading to serious legal and financial consequences.
8. How often should I scan my website for malware?
At minimum, scan weekly. Daily scans are recommended for high-traffic or e-commerce sites. Most security plugins allow automated scans with email alerts for any suspicious activity or file changes.
9. Can I restore my website from a backup after a malware attack?
Yes, restoring from a clean backup is one of the fastest ways to remove malware. Make sure the backup is from before the infection occurred. After restoring, immediately update everything and improve your security measures to prevent reinfection.
10. How can I prevent malware from coming back to my website?
Prevention includes:
- Keeping software up to date
- Using strong, unique passwords
- Limiting admin access
- Installing firewalls and security plugins
- Regularly backing up data
- Monitoring site activity
- Hosting with a secure provider
Proactive security and routine maintenance are key to long-term protection.