
Posted on October 30, 2025 by DhirenR.
A hacked website can be a nightmare, leading to data loss, SEO damage, and a loss of trust among visitors. If site has been compromised, immediate action is important to minimize the damage and restore security. Dealing with malware, defaced pages, or unauthorized access, this step-by-step guide will help you recover a hacked website efficiently. […]

Posted on October 30, 2025 by DhirenR.
In today’s competitive SaaS landscape, selecting the right SaaS billing software is more than just about managing invoices—it’s about streamlining the entire subscription lifecycle. From automating billing and tax compliance to reducing churn and improving analytics, the right billing solution can drive sustainable growth for any startup. As a SaaS expert and startup advisor, I’ve […]

Posted on October 30, 2025 by DhirenR.
Cloud computing has revolutionized the way individuals and organizations manage data, applications, and infrastructure. With flexible storage, scalable computing power, and on-demand resources, cloud computing is the foundation of digital transformation in nearly every sector. But for beginners, the wide variety of terms, models, and services can be confusing. This article breaks down the types […]

Posted on July 18, 2025 by DhirenR.
Website owners, developers, and businesses are facing an unprecedented surge in cybersecurity risks. The digital world has turned increasingly hostile—not just because the number of attacks has risen, but because these attacks have grown more intelligent, scalable, and targeted. Gone are the days of simple brute-force or spam-based intrusions. Today’s Website Security Threats are intelligent […]

Posted on July 15, 2025 by DhirenR.
In rapidly evolving cyber threat landscape, merely having a website is no longer enough — protecting it is equally essential. With increasing incidents of ransomware attacks, phishing attempts, and brute-force logins, your website can become a prime target if not properly defended. This is where setting up firewalls plays a crucial role. A firewall is […]
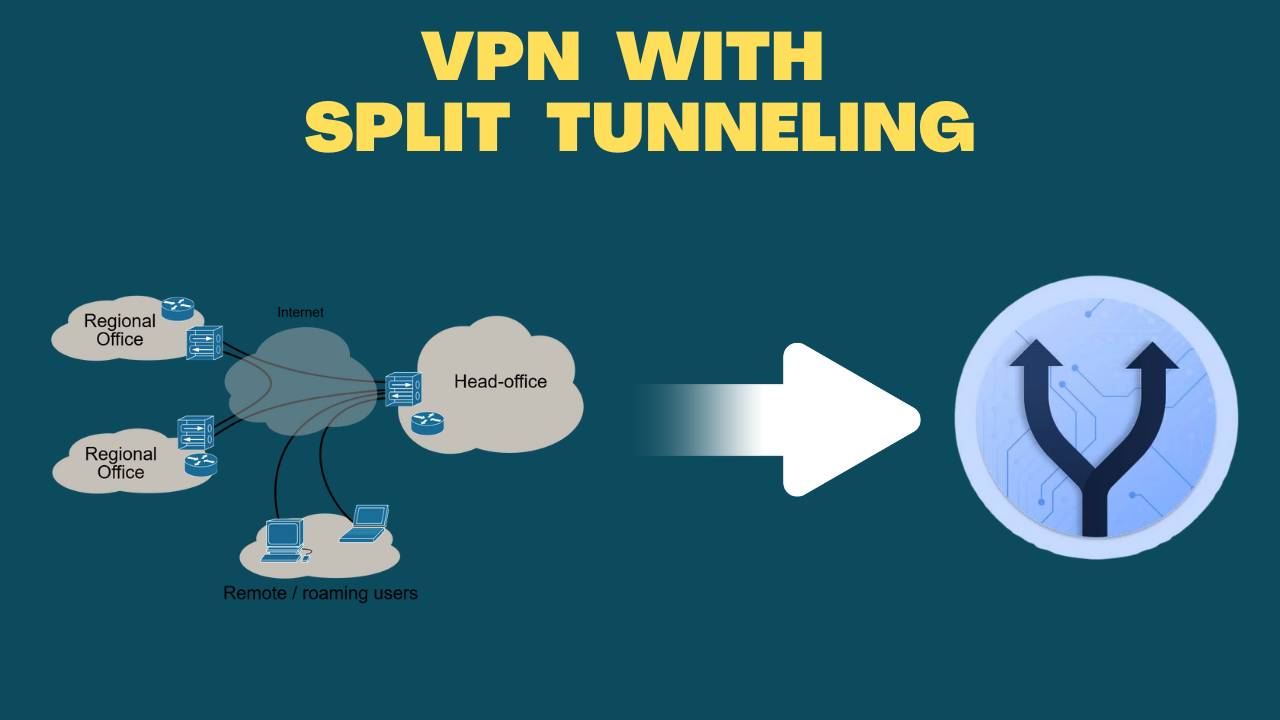
Posted on July 13, 2025 by DhirenR.
As digital demands continue to rise in 2025, so does the need for smarter internet security and optimized connectivity. For professionals working remotely, gamers wanting low latency, or streamers juggling multiple services, the ability to control internet traffic selectively has become a game-changer. That’s where a VPN with split tunneling steps in—offering flexibility, privacy, and […]

Posted on July 13, 2025 by DhirenR.
In the digital age, where nearly every action we take involves the internet—whether browsing, banking, or simply watching videos—privacy and security have become more crucial than ever. One emerging technology that aims to protect internet users from surveillance, DNS spoofing, and censorship is DNS over HTTPS (often abbreviated as DoH). How to Get HTTPS for […]
Posted on July 12, 2025 by DhirenR.
While HTTPS encrypts the content of websites you visit, your DNS (Domain Name System) queries often remain exposed—making them a prime target for hackers, surveillance agencies, and ISPs looking to track your activity. That’s where DNS over HTTPS (DoH) and DNS over TLS (DoT) step in as modern solutions to secure DNS communication. DNS over […]

Posted on March 2, 2025 by PMslTech
WordPress, while incredibly popular, is often targeted by hackers looking to compromise sites for phishing, malware distribution, or other malicious activities. If your website has been hacked or compromised, it can impact not only your site’s functionality but also your visitors’ trust and your site’s SEO. This cover two important aspects of WordPress security: first, […]

Posted on February 24, 2025 by PMslTech
The usage statistics posted on a number of websites clearly depict the popularity and relevance of PHP as a server-side programming language in 2018. There are a number of programming languages that enable developers to build custom web applications with concise, readable, and maintainable code base. But PHP, unlike other programming languages, accelerates custom web […]









